Tom Brewster
theguardian.com, Monday 2 June 2014 16.10 BST
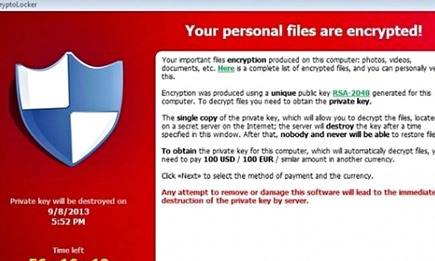
CryptoLocker will encrypt files with a public key that is widely seen as unbreakable. CryptoLocker will encrypt files with a public key that is widely seen as unbreakable.
Digital police from across the globe have claimed success in disrupting a criminal operation running one of the most aggressive computer viruses ever seen, known as CryptoLocker.
The UK's National Crime Agency (NCA) has warned British internet users that they have a two-week window to protect themselves from the malware, after working with the FBI, Europol and other law enforcement bodies to weaken the global network of infected computers.
The CryptoLocker software locked PC users out of their machines, encrypting all their files and demanding payment of one Bitcoin (currently worth around £300) for decryption.
It’s believed CryptoLocker, which the FBI estimated acquired $27m in ransom payments in just the first two months of its life, has infected more than 234,000 machines.
A chief suspect from Russia has been identified, but is still at large, Troels Oerting, head of Europol's European Cyber Crime Centre (EC3) told the Guardian. He said other arrests related to the operation were “in progress”.
The global effort to stop the spread of the CryptoLocker ransomware has focused on its delivery method, itself a dangerous form of malware called Gameover Zeus (GOZeuS), which connected infected machines by peer-to-peer connections – in theory making it harder for the authorities to track and stop.
GOZeuS was designed to steal people's online banking login details, who were usually infected by clicking on attachments or links in emails that looked innocuous. However, it also dropped CryptoLocker on their computers.
"Nobody wants their personal financial details, business information or photographs of loved ones to be stolen or held to ransom by criminals," said Andy Archibald, deputy director of the NCA's National Cyber Crime Unit.
"By making use of this two-week window, huge numbers of people in the UK can stop that from happening to them. Whether you find online security complicated or confusing, or simply haven’t thought about keeping your personal or office computers safe for a while, now is the time to take action."
Affected users are being advised to update their operating system software and security software, and also to "think twice before clicking on links or attachments in unsolicited emails".
Not-for-profit body Get Safe Online has worked with the NCA to launch a dedicated section of its website to provide guidance and tools, although at the time of publication the website appeared to be offline.
Behind the scenes, the law enforcement groups have been taking over points of control in GOZeuS's peer-to-peer network: an action known as "sinkholing" in the security world. By doing this, they have been able to cut off criminal control over the infected computers.
Dismantling peer-to-peer operated malware is difficult, but it has been done before: for example one case of a data-stealing virus called ZeroAccess, which infected as many as 1.9m PCs in 2013.
In that case, security researchers from Symantec managed to send lists of fake peers to infected machines, which meant they could no longer receive commands from the controllers of the malicious network, known as a botnet.
Symantec researchers said today that key nodes in GOZeuS' network had been disabled, along with a number of the domains used by the attackers.
Oerting told the Guardian the entire GOZeuS operation’s infrastructure had been sinkholed, meaning the malware should “not reappear for … considerable time”.
US authorities have identified Evgeniy Mikhailovich Bogachev, 30, of Anapa in the Russian Federation, as the leader of the criminal operation behind GOZeuS, which is thought to have infected between 500,000 and 1m computers worldwide, including more than 15,500 in the UK.
Many of those machines will also be infected by CryptoLocker. Victims are likely to receive messages from their ISPs in the coming weeks alerting them of infection.
Although arrests have not yet been made, Oerting believes the eventual impact will be “great”. “[It will not last] forever, but the infrastructure is gone and the criminals will have to build and distribute from scratch,” he added.
http://www.theguardian.com/technology/2 ... protection